Previous
How Does One – Click Attack Manipulate Anything ?
Invalid Name
Invalid Email
Invalid Phone Number
This can't be empty
Sept 25 2021
The first course in the learning path covers workstation setup, including installation and configuration of Burp Suite with the Firefox web browser. Certificate installation and proxy configurations are covered in order to allow newcomers to start pentesting immediately. The second course makes up the bulk of this learning path and focuses on the OWASP Top Ten vulnerabilities. Many real-world vulnerabilities are showcased for each of the ten topics and various demos are given on how to solve related challenges in both OWASP Juice Shop and Portswigger’s Web Security Academy. The third course covers a variety of pentesting tools and Burp extensions such as Turbo Intruder, Intruder File Payload Generator, SQLMap and many more. The fourth course closes out the learning path with pentesting advice, a path recap and a look at the final project
As Internet usage is rising day by day security has become a vital facet to the Internet world. Security of the website in today's world is very important. Vulnerability Assessment and Penetration Testing are two different vulnerability testing. These tests have different strengths and are frequently combined to get a more complete vulnerability analysis. Penetration Testing and Vulnerability Assessments execute two different tasks, usually with distinctive outcomes, within the same area of application. For any organization, proper working of security arrangement is checked by Vulnerability Assessment and Penetration Testing. Web applications vulnerable to attacks like Session exploitation, Cross-Site Scripting, SQL injection, Cross Site Request Forgery, Buffer overFlows, and Security Misconfiguration etc. are described in Open Web Application Security Project Top 10. The manual penetration test or an automatic penetration test can be done, which depends upon vulnerabilities. Comparison is made between these two tests.
Very often, automated vulnerability scanners fail to pick up on more subtle security flaws. An experienced assessor will understand the context of the application and may figure out how to abuse its logic. Many of these vulnerabilities are simply not picked up by automated tools.
The expert security engineers of swfitsafe often make use of vulnerability scanners in the preliminary phases of an application security test, though it is only in the beginning. With a greater understanding of the application’s context, we can provide assessments that are more relevant to your user-base and individual security needs.
Almost everything that we do is done through the internet. From shopping to banking to everyday transactions, most of them can be done digitally. And there are several web applications that can be used to complete these online activities. The popularity of web applications has also introduced another vector of attack that malicious third parties can exploit for their personal gains. Since web applications usually store or send out sensitive data, it is crucial to keep these apps secure at all time, particularly those that are publicly exposed to the World Wide Web.
In a nutshell, penetration testing is a preventive control measure that lets you analyze the overall status of the existing security layer of a system.
These are the common goals of doing pen testing for web apps:
1. Identify unknown vulnerabilities
2. Check the effectiveness of the existing security policies
3. Test publicly exposed components, including firewalls, rout
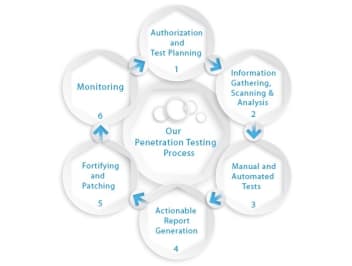
swiftsafe operates under a structured, repeatable methodology. We prioritize this concept in each engagement to make certain that our assessment is reliable, reproducible, and top-notch in quality. As such, our findings can always be verified by your team, before and after the remediation. To get these results, we are guided by the following steps:
1 – Define Scope
Before a web application assessment can take place, swfitsafe defines a clear scope of the client. Open communication between swfitsafe and the client organization is encouraged at this stage to establish a comfortable foundation from which to assess. • Determine which of the organization’s applications or domains are to be scanned/tested
• Make exclusions from the assessment known (specific pages/subdomains)
• Decide on the official testing period and confirm time zones
2 – Information Gathering
Swfitsafe engineers collect as much information as they can on the target, employing a myriad of OSINT (Open Source Intelligence) tools and techniques. The gathered data will help us to understand the operating conditions of the organization, which allows us to assess risk accurately as the engagement progresses. Targeted intelligence might include:
• PDF, DOCX, XLSX, and other files leaked by Google
• Previous breaches/credential leaks
• Revealing forum posts by application developers
• Exposed robots.txt file
3 – Enumeration
At this stage, we incorporate automated scripts and tools, among other tactics in more advanced information gathering. swfitsafe engineers closely examine any possible attack vectors. The gathered information from this stage will be the basis for our exploitation in the next phase. • Enumerating directories/subdomains
• Checking cloud services for possible misconfigurations
• Correlating known vulnerabilities with the application and relevant services
4 – Attack and Penetration
With careful consideration, we begin to attack vulnerabilities found within the webapp. This is done cautiously to protect the application and its data, while still verifying the existence of discovered attack vectors. At this stage, we may perform attacks such as:
• SQL injection and/or Cross-Site Scripting
• Employing breached credentials and brute force tools against authorization mechanisms
• Monitoring web app functionality for insecure protocols and functions
5 – Reporting
Reporting is the final stage of the assessment process. swfitsafe analysts aggregate all obtained information and provide the client with a thorough, comprehensive detailing of our findings. The report begins with a high-level breakdown of the overall risk, highlighting both strengths and weaknesses in the application’s protective systems and logic. We also include strategic recommendations to aid business leaders in making informed decisions regarding the application. Further into the report, we break down each vulnerability in technical detail, including our testing process and remediation steps for the IT team, making for a simple remediation process. We go to great lengths to ensure each report is both explicit and easy to navigate.
6 – Remediation Testing
Additionally, upon client request, swfitsafe may review an assessment after the client organization has patched vulnerabilities. We will ensure changes were implemented properly, and the risk has been eliminated. The previous assessment will be updated to reflect the more secure state of the application.
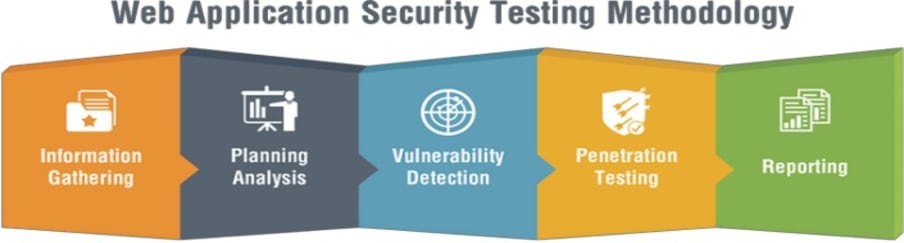
Penetration testing is a series of activities undertaken to identify and exploit security vulnerabilities. It helps confirm the effectiveness or ineffectiveness of the security measures that have been implemented. It discusses the benefits, the strategies and the methodology of conducting penetration testing. The methodology of penetration testing includes three phases: test preparation, test and test analysis. The test phase involves the following steps: information gathering, vulnerability analysis, and vulnerability exploit.
With us, you can strengthen the security system of your organization and add financial value to the business.
Very urgent? Call us at +1 657-221-1565
Invalid Name
Invalid Email
Invalid Phone Number
This can't be empty
With us, you can strengthen the security system of your organization and add financial value to the business.
Very urgent? Call us at +1 657-221-1565
Invalid Name
Invalid Email
Invalid Phone Number
This can't be empty